PSI employees with an account can use the system as standard. Non-PSI employees must apply for an account for external users via their responsible contact person.
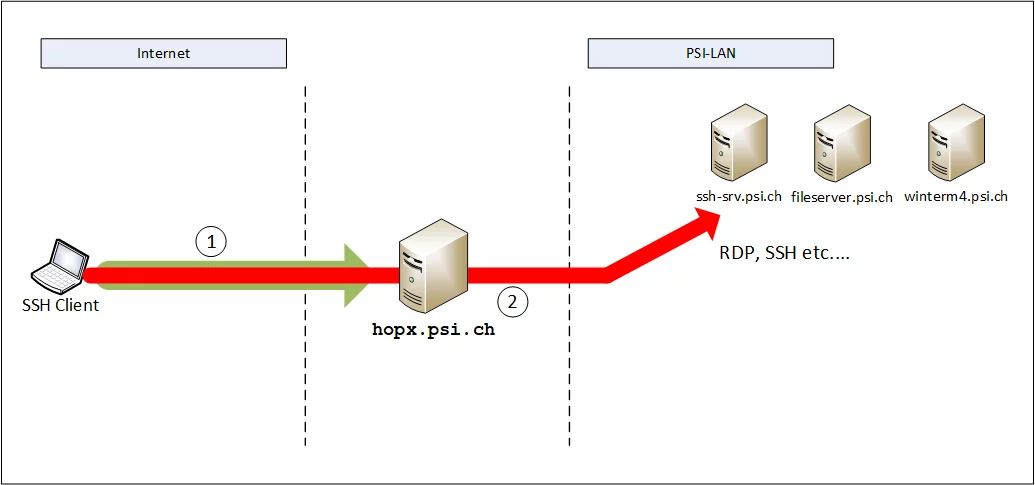
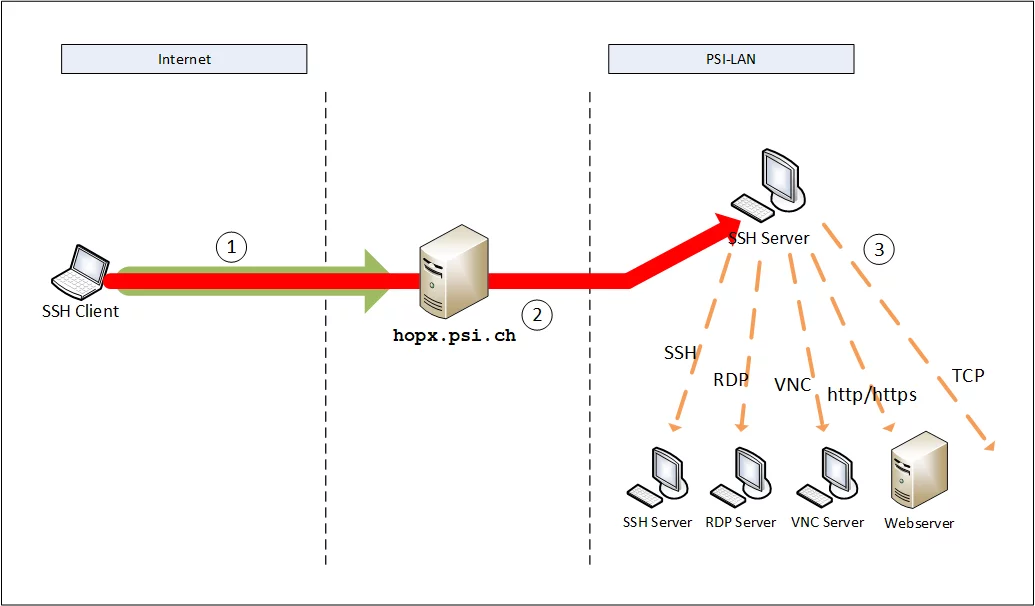
The system is only available as a tunnelling/proxy system. This means that after successfully logging into the system, there is NO active, usable shell available that can be used for a further connection to the PSI Lan.
A ‘setup-connection’ to hopx.psi.ch must be established at the start of use. This connection sets up access for the user on hopx.psi.ch. It must be interactive and kept open. Without this ‘setup-connection’, no connections to PSI-Lan are possible via hopx.psi.ch!
- Only one active ‘setup-connection’ to
hopx.psi.chis possible per user. (further information can be found below) - the ‘setup-connection’ can be combined with one or more port forwarding (see below)
- SSH clients (Putty, OpenSSH etc.) can be configured so that SSH connections to the PSI LAN are made via the ‘setup-connection’. (Keyword: SSH multiplexing, ProxyJump, Connection Sharing)
Note on OpenSSH:
The command
ssh -J <user>@hopx.psi.ch <user>@example-ssh-srv.psi.ch
does not work without a prior ‘setup-connection’, even if this is usually possible with OpenSSH!!!!
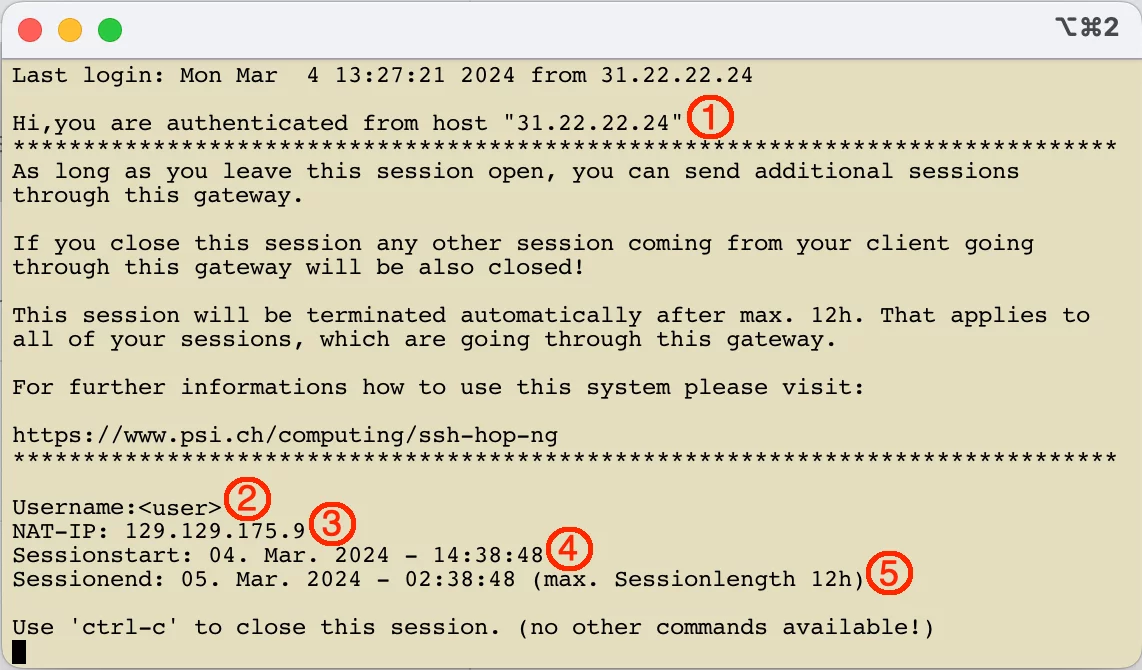
The following illustration shows the output after successful login.
The output after the login contains the following important information:
- The IP address of the client which established the connection to
hopx.psi.ch. - The user name which is used for the connection.
- The NAT IP address, which will be used for the connections established by the user through
hopx.psi.chto systems within the PSI network. - The date and time when the connection to
hopx.psi.chwas started - The maximum date and time until which the connection to
hopx.psi.chcan be held open. At this time (if the maximum session duration of 12 hours has expired) the connection tohopx.psi.chis automatically terminated. All connections to the PSI network going throughhopx.psi.chwill also be disconnected.
The connection to hopx.psi.ch can be terminated with ‘ctrl-c’. No further commands are available!
********* Attention ****************
If the ‘setup-connection’ to hopx.psi.ch is terminated while the connection(s) to an internal system are still active/open, these will also be terminated!!!
*********************************
Behaviour when establishing more than one ‘setup-connection’
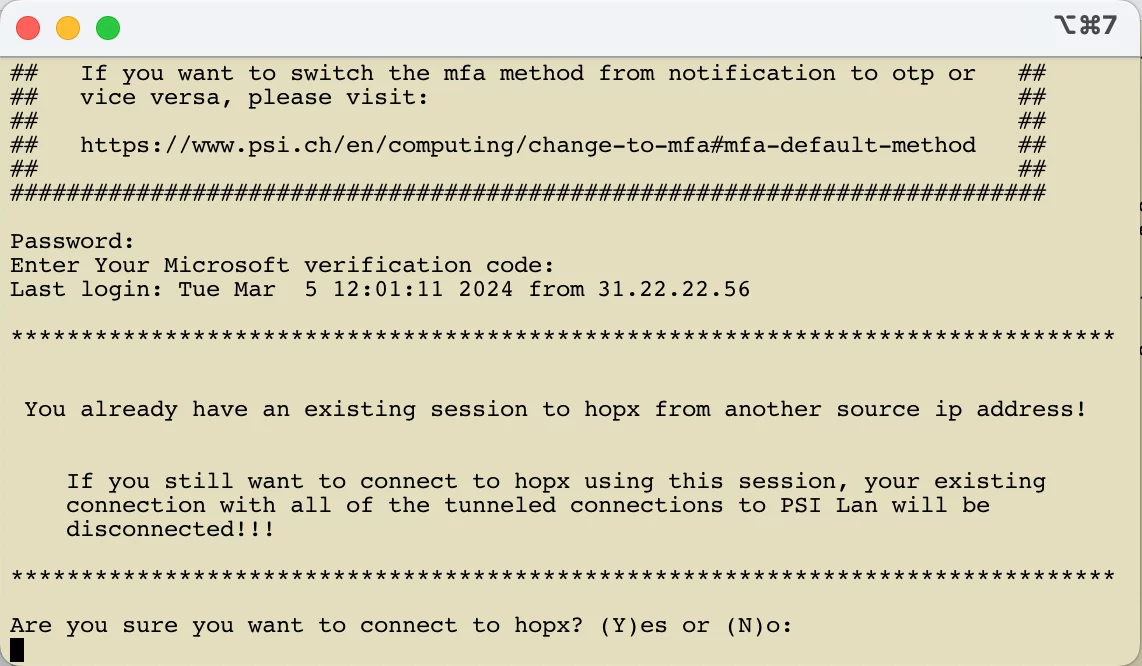
If a second ‘setup-connection’ is established to hopx.psi.ch using the same user name and the same source IP address, this connection will be terminated after successful authentication with a reference to the existing connection.
If a second ‘setup-connection’ is established to hopx.psi.ch using the same user name but a different source IP address to the existing connection, the user is given a choice after successful authentication. He can actually establish the second connection, but then the first connection and all associated tunnelled connections to the PSI network will be disconnected. Or he can terminate the second connection and continue working with the first. The answer to the question must be ‘Y’, ‘y’, ‘N’ or ‘n’.
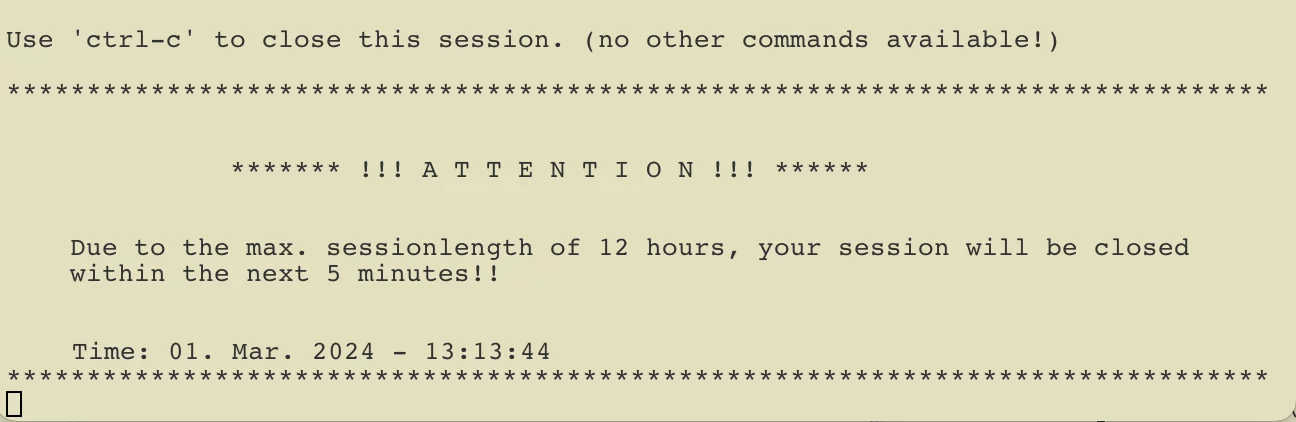
Maximum session duration of 12 hours
The duration of the active connection to hopx.psi.ch is limited to a maximum of 12 hours, similar to VPN access. The maximum time until which the connection can remain active is displayed after an successful authentication (see above). In the same window, five minutes before the connection is terminated, a message is displayed indicating that the connection is about to be terminated.
********* Attention ****************
If the connection to hopx.psi.ch is terminated while the connection(s) to an internal system are still active/open, then all other connections will also be terminated when the connection to hopx.psi.ch is terminated!!!!
***********************************
Note on the possible tunnel connections
Please note that not all users of the system have the same access rights. Depending on the type of the user account, different connections are possible via the system.
PSI employees
PSI employees can tunnel the following TCP connection to the PSI LAN via hopx.psi.ch:
| TCP port number | is used by |
|---|---|
| 22 | SSH |
| 80/443 | HTTP(S) |
| 445 | Windows File Server (z. B. fs00, fs01 or fs02) |
| >1023 | e.g. für RDP, VNC etc. |
External users
External users can tunnel the following TCP connection to the PSI LAN via hopx.psi.ch:
- SSH connections to the
Merlin,RA,Login,MEGetc. clusters. - SSH connections to the experiment jump systems etc.
These SSH connections are only possible if you have the appropriate access rights. If you do not have these rights, please get in touch with your responsible PSI contact person.
If you require further connection options, these must be requested for you by your PSI contact person.
The previously generally valid access options for external users such as
| TCP port number | is used by |
|---|---|
| 22 | SSH |
| 3389 | RDP |
| 5900 | VNC |
will be gradually deactivated during the next weeks.
Note on the use of VS Code
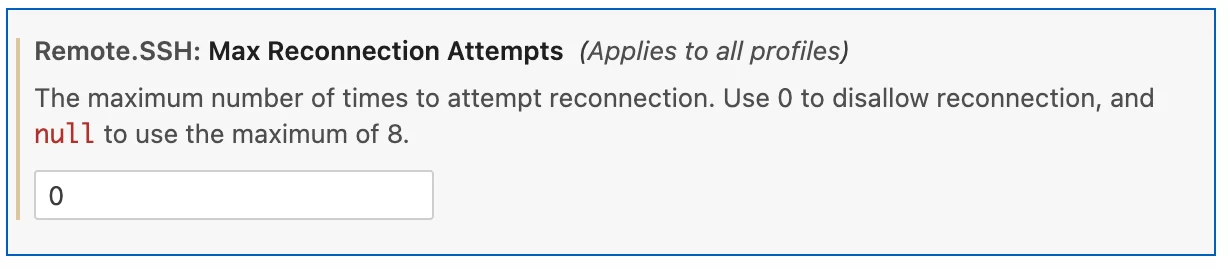
The remote SSH plugin of VS Code tries to re-establish an interrupted SSH connection several times due to the default settings. If a user was connected to several systems remotely via SSH and the connections were interrupted, VS Code tries to re-establish each connection automatically. This behavior can lead to many failed login attempts on hopx.psi.ch and in extreme cases to an automated blocking of the user account or the client IP address.
To prevent this, the number of automated connection attempts in the VS code must be significantly reduced.
To do this, "Max Reconnection Attempts" must be set to 0:
SSH, RDP etc. to internal systems with the help of port forwarding
Recommended for users who want to quickly establish an RDP or SSH connection to a system in the PSI LAN.
Use case:
- Forwarding of one or more ports via
hopx.psi.chto an internal system for the use of RDP, SSH etc.
Advantage:
- fast access to an internal system, as it is not necessary to set up Putty Connection Sharing (see below)
- only one connection (setup-connection, see basics above) with simultaneous port forwarding to
hopx.psi.chnecessary - no Putty version >= 0.78 required on the client system
Disadvantage:
- if there is already a connection to
hopx.psi.chand you want to forward another local port, the connection tohopx.psi.chmust first be terminated and re-established.
Proceed as follows for the configuration:
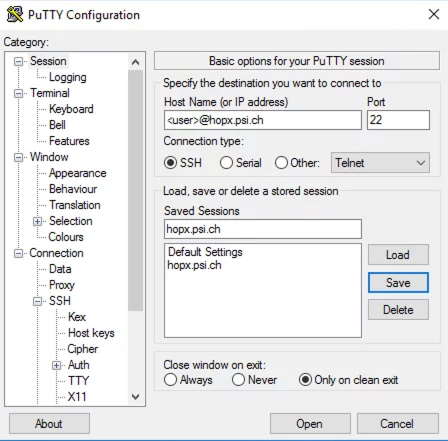
Start Putty and select the upper entry “Session” in the left column “Category”, fill in the "Host Name (or IP address)" field on the right
<user>@hopx.psi.ch
(please replace <user> with the actual user name)
Enter a name for this profile in the "Saved Session" field. In this case "hopx.psi.ch" (do not click on Save yet )
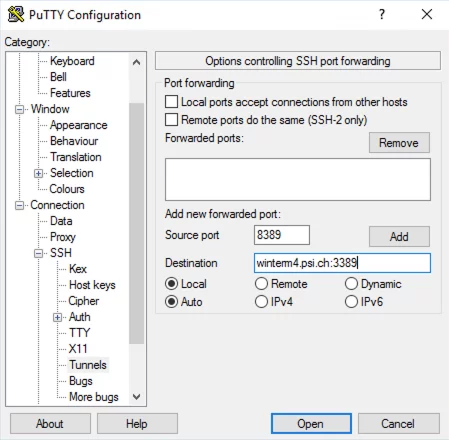
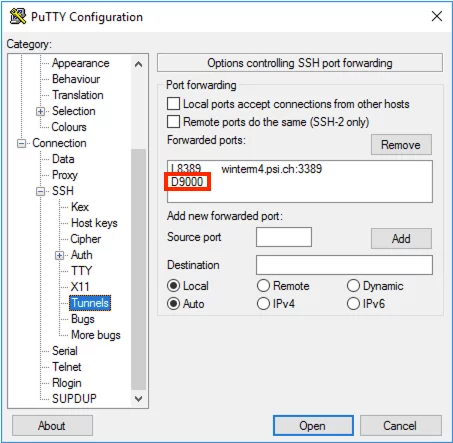
Then select “Connection -> SSH -> Tunnels” in the left-hand column. Then enter e. g. the local port “8389” in the “Source port” field, and the destination server and the corresponding port “winterm4.psi.ch:3389” in the “Destination” field. The type is set to “Local” and then “Add” is clicked. With this setting, RDP connections to the local port 8389 are directed to winterm4.psi.ch port 3389.
After the tunnel configuration is complete, it will look like this.
Then go back to “Session” and save the settings by clicking “Save”.
To use the previously created configuration, proceed as follows:
- Establish an SSH connection (setup-connection, see Basics) with port forwarding to
hopx.psi.ch - Use the port forwarding
Example: Step no. 1, setting up a setup-connection to hopx.psi.ch with port forwarding
Select the saved connection “hopx.psi.ch”, click “Load” and then “Open”. As soon as the connection to hopx.psi.ch is established after an successful authentication, step no. 2 takes place
Example: Step no. 2, use the port forwarding
If the connection to hopx.psi.ch is established, the connection to the internal system can then be established via the locally forwarded port. Start the RDP client and connect with “localhost:8389” or “127.0.0.1:8389” to reach the login prompt of winterm4.psi.ch.
SSH to one or more internal systems using “Connection sharing”
Recommended for users who regularly want to establish an SSH connection to several internal systems
Use case:
- Establishing one or more SSH connections via
hopx.psi.chto internal systems.
Advantage:
- no port forwarding to the internal systems necessary
- flexible establishment of one or more SSH connections to internal systems, as no adaptation of port forwarding is necessary
Disadvantage:
- without activated connection sharing, authentication to
hopx.psi.chis required for every connection (setup-connection and connections to internal systems)
Note:
Connection sharing is not available for Putty versions lower than 0.78 and can only be used for port forwarding in conjunction with hopx.psi.ch.
In the “Category” column on the left, select the “Session” entry at the top and in the “Host Name (or IP address)” field on the right fill in
<user>@hopx.psi.ch
(please replace <user> with the actual user name)
Enter a name for this profile in the “Saved Session” field. In this case “hopx.psi.ch” (do not click “Save” yet)
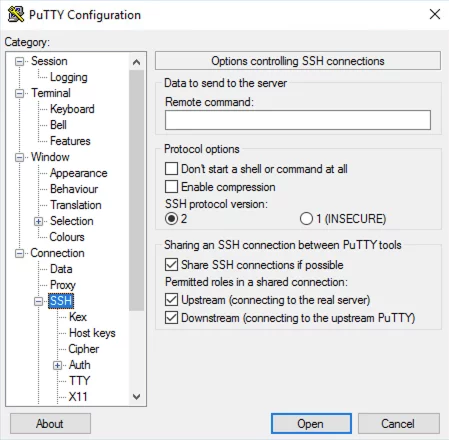
Then select the “Connection -> SSH” entry in the “Category” column on the left and check the “Share SSH connections if possible” box under “Sharing an SSH connection between PuTTY tools”.
Now the settings must be saved. In the “Category” column on the left, select the “Session” entry at the top and click “Save” on the right. The preparation for the connection to hopx.psi.ch is now complete.
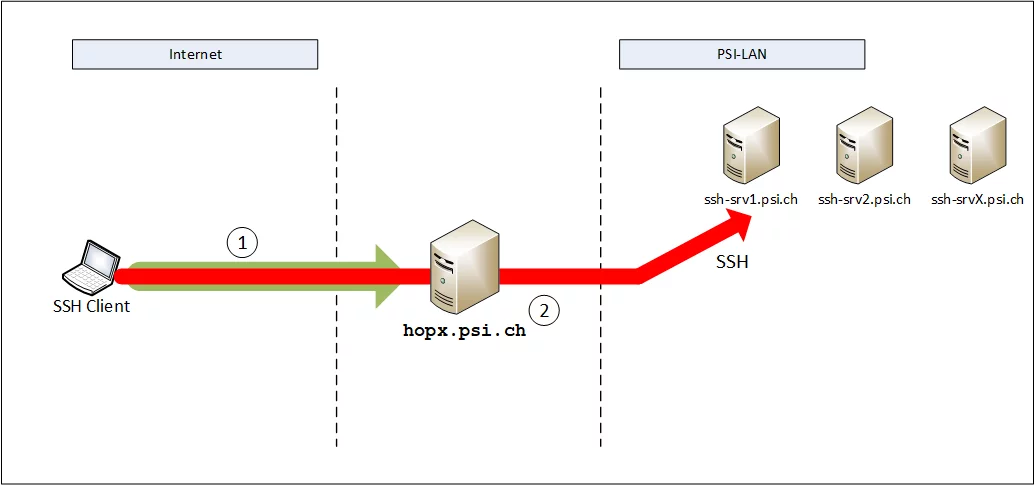
To connect to the internal system (e.g. to ssh-srv1.psi.ch), proceed as follows:
(Note: ssh-srv1.psi.ch, ssh-srv2.psi.ch etc. are not real systems, merely placeholders and serve as examples. These host names must be replaced by the host name of the system you know!)
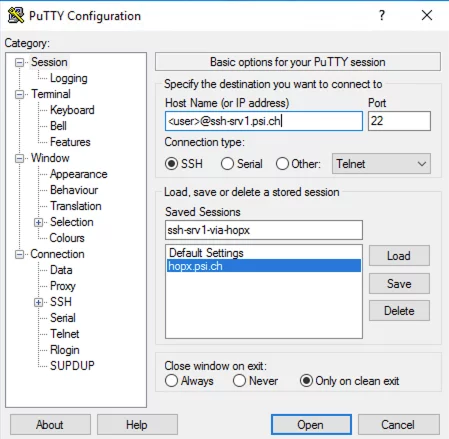
In the “Category” column on the left, select the “Session” entry at the top and in the “Host Name (or IP address)” field on the right fill in
<user>@ssh-srv1.psi.ch
(please replace <user> with the actual user name)
Enter a name for this profile in the “Saved Session” field. In this case “ssh-srv1-via-hopx” (do not click “Save” yet)
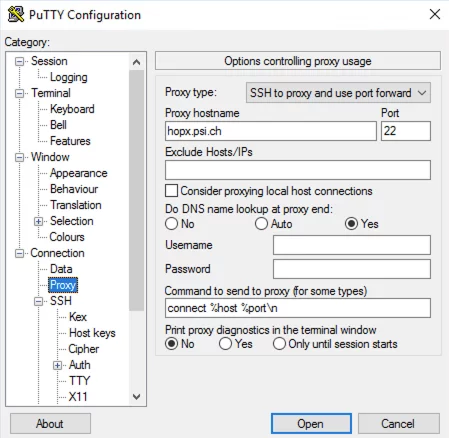
In order to connect to ssh-srv1.psi.ch via hopx.psi.ch, the entry “Connection -> Proxy” must be selected in the “Category” column on the left. In the right part of the Putty window, “Proxy type” must be set to “SSH to proxy and use port forwarding”. “hopx.psi.ch” must be entered in the "Proxy hostname" field and "22" must be entered in the "Port" field.
(Note: The name in the “Proxy hostname” field must match the name saved under “Saved Session” (see above) for hopx. In this case “hopx.psi.ch”. If the connection profile for hopx was saved under a different name, the entry must be adjusted here).
In the line “Do DNS name lookup at proxy end” must be changed from “Auto” to “Yes”.
Then go back to “Session” and save the settings by clicking “Save”.
To use the previously created configuration, proceed as follows:
- establish a SSH connection (setup-connection, see Basics) to
hopx.psi.chand leave it open - establish a SSH connection via
hopx.psi.chto the internal system (ssh-srv1.psi.ch)
Example: Step no. 1, establish setup-connection to hopx.psi.ch
Select the saved connection “hopx.psi.ch”, click “Load” and then “Open”. As soon as the connection to hopx.psi.ch is established after an successful authentication, step no. 2 takes place
Example: Step no. 2, establish SSH connection to the internal system ssh-srv1.psi.ch
Call Putty again and select the saved connection “ssh-srv1.psi.ch”, click “Load” and then “Open”. If everything has been configured correctly, you will now see the login prompt of ssh-srv1.psi.ch, where you have to authenticate yourself. (A new call for authentication at hopx.psi.ch, before authentication at ssh-srv1.psi.ch, should not take place).
A new connection profile must be created in Putty for each connection to another internal SSH server. The easiest way to do this is with the following steps:
- select an already saved connection, e.g. “
ssh-srv1.psi.ch” and click “Load” - adjust the “
Host Name (or IP address)” field, e.g.<user>@ssh-srv2.psi.ch - enter a name for this profile in the “
Saved Session” field. In this case “ssh-srv2-via-hopx” and click “Save”
SSH using “Connection sharing” and simultaneous port forwarding via an internal system
Recommended for users who regularly want to establish an SSH connection to several internal systems and one or more other connections (e.g. RDP, file server, etc.) to other internal systems in parallel.
To use port forwarding, only the example described above for “SSH to one or more internal systems using connection sharing” needs to be supplemented with port forwarding for RDP.
For example, for port forwarding to winterm4.psi.ch via the SSH connection to ssh-srv1.psi.ch, proceed as follows:
In the “Category” column on the left, select the existing profile “ssh-srv1.psi.ch” under “Session” and click “Load”. Then select “Connection -> SSH -> Tunnels” in the left-hand column. Then enter the local port “8389” in the “Source port” field, and the destination server and the corresponding port “winterm4.psi.ch:3389” in the “Destination” field. The type is set to “Local” and then “Add” is clicked. With this setting, RDP connections to the local port 8389 are directed to winterm4.psi.ch port 3389.
After the tunnel configuration is complete, it will look like this.
Then go back to “Session” and save the settings by clicking “Save”.
To use the previously created configuration, proceed as follows:
- establish an SSH connection (setup-connection, see Basics) to
hopx.psi.chand leave it open - establish an SSH connection via
hopx.psi.chto the internal system (ssh-srv1.psi.ch) (starts port forwarding, among other things) - use the port forwarding
Example: Step no. 1, establish setup-connection to hopx.psi.ch
Select the saved connection “hopx.psi.ch”, click “Load” and then “Open”. As soon as the connection to hopx.psi.ch is established after successful authentication, step no. 2 takes place
Example: Step no. 2, establish SSH connection to the internal system ssh-srv1.psi.ch
Call Putty again and select the saved connection “ssh-srv1.psi.ch”, click “Load” and then “Open”. If everything has been configured correctly, you will now see the login prompt of ssh-srv1.psi.ch, where you have to authenticate yourself. (A new call for authentication at hopx.psi.ch, before authentication at ssh-srv1.psi.ch, should not take place).
Example: Step no. 3, using port forwarding
If you then start the RDP client and connect with “localhost:8389” or “127.0.0.1:8389”, you will reach the login prompt of winterm4.psi.ch.
Dynamic tunneling
With dynamic tunneling, hopx.psi.ch or a system in the internal PSI network is used as a Socks5 proxy. In conjunction with a browser, which then sends the requests to the Socks5 proxy, several different internal web servers/websites can be contacted.
Dynamic tunneling is configured in Putty with the help of port forwarding. This can be done via hopx.psi.ch, as described in the section “SSH, RDP etc. to internal systems using port forwarding”. Or it can be done via an internal system as described in the section “SSH using ‘Connection Sharing’ and simultaneous port forwarding via an internal system”.
In Putty, a saved connection (either to hopx.psi.ch or an internal system) must be selected under “Session”, then click “Load”. Then select “Connection -> SSH -> Tunnels” in the left-hand column. Then enter e.g. the local port “9000” in the “Source port” field and leave the “Destination” field empty. The type is set to “Dynamic” and then “Add” is clicked. Then save the change to the saved session under “Session” by clicking “Save”.
It is important for the user to distinguish at which connection with Putty the local port 9000 is opened for forwarding. Either during the connection to hopx.psi.ch or only during the second connection via hopx to an internal system in the PSI network.
Use of dynamic tunneling
Once an SSH connection has been established with Putty to hopx.psi.ch or a system in the internal PSI network and port 9000 is available locally, it can be used with a browser.
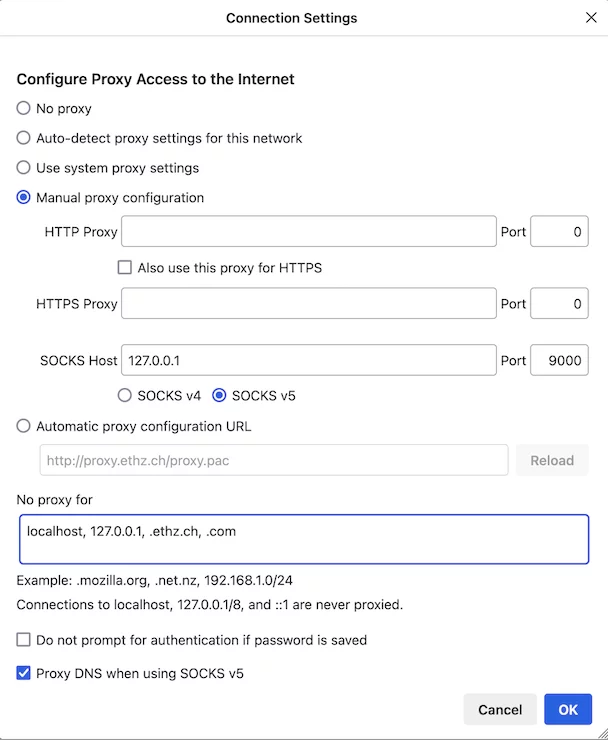
Now you can enter, e. g. in the proxy settings of the Firefox browser (Settings -> General -> Network) at
"SOCKS Host: localhost Port: 9000"
Instead of “localhost” you can also enter “127.0.0.1”.
In the "No Proxy for:" field, you should also enter all domain/host names, IP addresses/ranges that are to be called up directly, i.e. without the detour via hopx.psi.ch or the internal system, e.g. "localhost, 127.0.0.1, .ethz.ch, .com" .
The option “Proxy DNS when using SOCKS v5” must be activated with a tick. The settings must be confirmed by clicking “OK”.
Note:
PSI employees can only access PSI internal websites, www.psi.ch and intranet.psi.ch via hopx.psi.ch. Access to ServiceNOW should also work. Other PSI-owned but externally hosted sites can be authorised if required. Connections to non-PSI, external websites will not be forwarded! If you need unrestricted access to PSI's own websites (as if a system is used on site at PSI), we recommend dynamic tunneling via a PSI-internal system in the PSI network and NOT directly via hopx.psi.ch.
MobaXterm can be used to access the PSI LAN via hopx.psi.ch, but is not officially supported by PSI.
Nevertheless, we would like to provide various tips below that could be helpful when using MobaXterm.
SSH to one or more internal systems
Use case:
- Establishing one or more SSH connections via hopx.psi.ch to internal systems.
Advantage:
- Flexible establishment of one or more SSH connections to internal systems
Disadvantage:
- Multiple authentications to hopx.psi.ch necessary.
The following steps are required to establish an SSH connection to an internal system with MobaXterm.
- setup-connection to hopx.psi.ch
- Connection to the internal system via
hopx.psi.chas ‘SSH gateway’
Proceed as follows for the configuration:
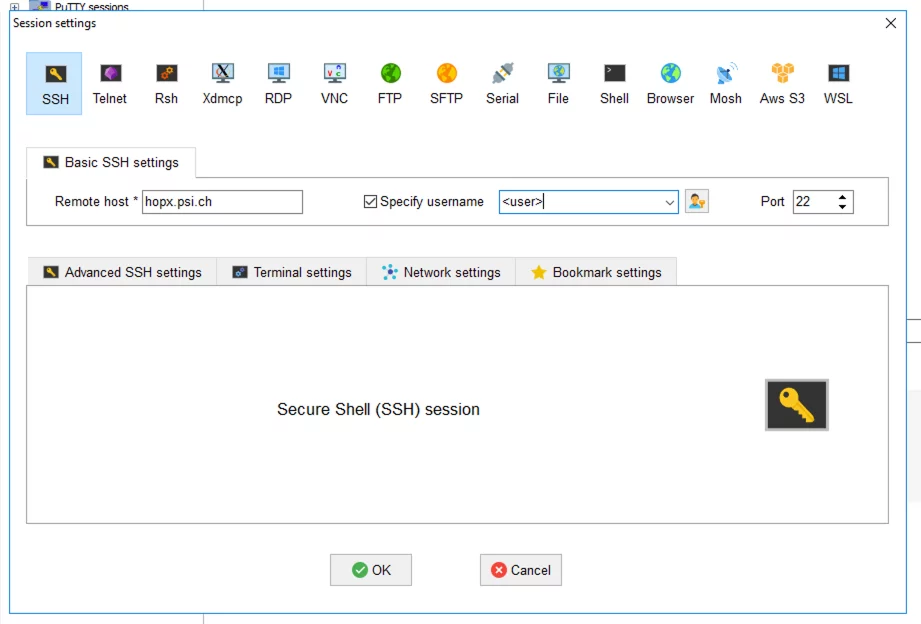
In the "Session-Settings" for SSH in "Basic SSH settings", enter hopx.psi.ch in the "Remote host" field. Tick Specify username, enter the user name in the field to the right and click OK at the bottom. The settings for the setup-connection are now complete.
The next step is to configure the SSH connection to the internal system.
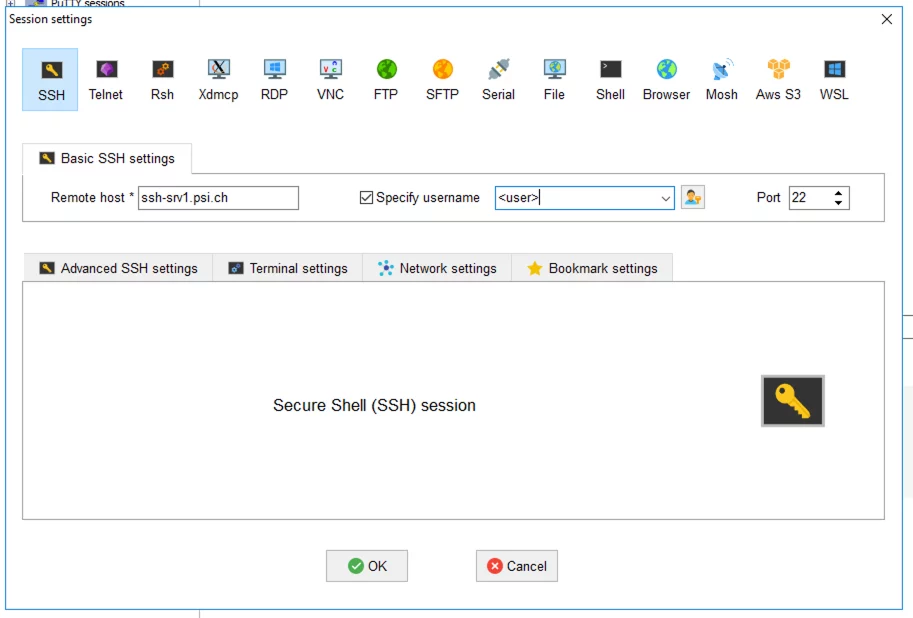
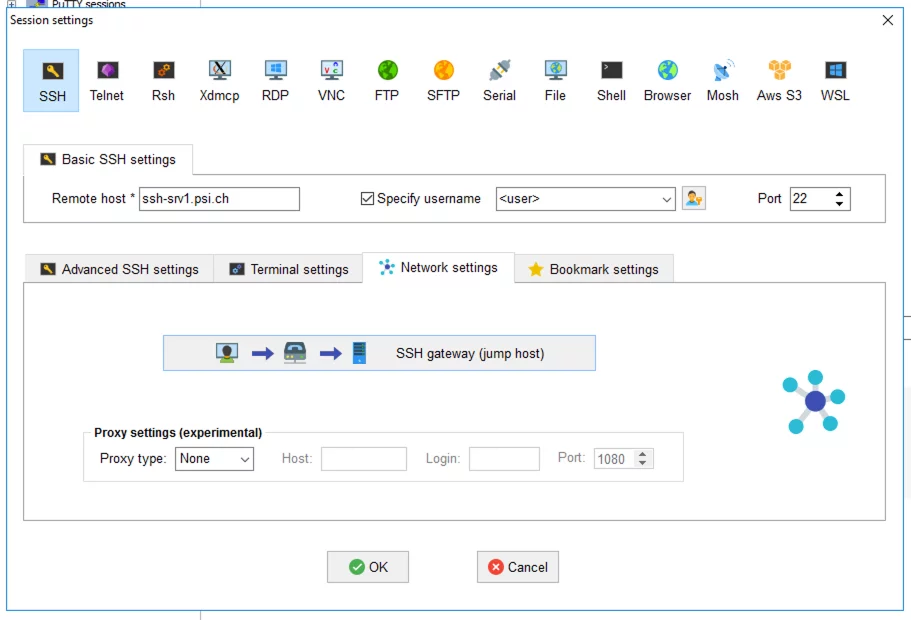
In the "Session-Settings" for SSH in "Basic SSH settings", enter the host name of the internal system (e.g. ssh-srv1.psi.ch) in the "Remote host" field.
(Note: ssh-srv1.psi.ch is not a real system, merely a placeholder and serves as an example. This host name must be replaced by the host name of the system you know!)
Then tick "Specify username" and enter the user name in the field to the right.
Click on the "Network settings" tab one line further down and then on "SSH gateway (jump host)".
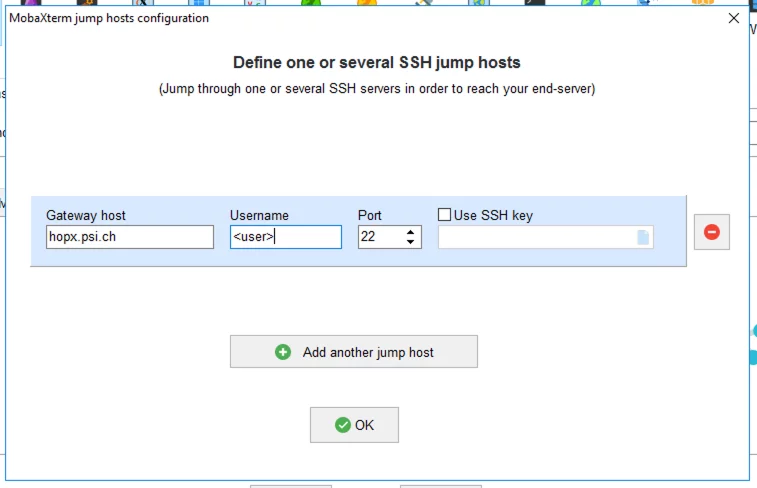
Enter hopx.psi.ch as the SSH gateway in the "Gateway host" field and the user name in the "Username" field. Then click "OK" at the bottom.
The configuration for the SSH connection to the internal system is now complete.
To use the previously created configuration, proceed as follows:
- establish an SSH connection (setup-connection, see Basics) to
hopx.psi.chand leave it open - establish an SSH connection via
hopx.psi.chto the internal system (ssh-srv1.psi.ch).
Note:
Step no. 1 with the establishment of the setup-connection to hopx.psi.ch must always be carried out separately! Establishing the connection from step no. 2 to the internal system via hopx.psi.ch as SSH gateway alone does not work!
Once the setup-connection to hopx.psi.ch has been successfully established, step no. 2, the establishment of the SSH connection to the internal system, takes place. As hopx.psi.ch was specified as the SSH gateway when the connection was configured, the connection is established via the existing setup-connection to hopx.psi.ch. Nevertheless, when establishing the connection to the internal system, you must first authenticate yourself again at hopx.psi.ch before you can access the login prompt of the internal system.
SSH with port forwarding / tunneling
How to configure port forwarding or tunneling in MobaXterm is not explained in detail here. However, we would like to point out that only two simultaneous forwardings are available for tunneling or port forwarding with MobaXterm in the free version of the software. More is not possible and requires the commercial version of the programme.
For users who want to use other client functions (RDP, VNC, file browser etc.) of MobaXterm from outside the PSI in addition to the SSH client function, we recommend the following procedure
Establish a setup-connection with Putty and start all necessary port forwarding. The procedure for this is described under ‘SSH, RDP etc. to internal systems using port forwarding’.
Use MobaXterm and the corresponding client functions to access the local ports forwarded from step no. 1.
SSH access via hopx.psi.ch to the PSI LAN can be used via SSH with Powershell, but is not officially supported by PSI. Please refer to the description for use with Unix/Linux/macOS.
But beware, even if the SSH version from Windows 10 is based on OpenSSH, not all features of the original have been implemented.
SSH multiplexing has not been implemented in the Windows version. More information can be found here. Even if the ControlPath is specified in the config file, this information is not used by the programme. This means that, e. g. for a second SSH connection via hopx.psi.ch (after setting up the separate setup-session!) with the command
ssh -J <user>@hopx.psi.ch <user>@ssh-srv1.psi.ch
re-authentication to hopx.psi.ch is necessary before reaching the login prompt of ssh-srv1.psi.ch.
(Note: ssh-srv1.psi.ch is not a real system, only a placeholder and serves as an example. This host name must be replaced by the host name of the system you know!)