PSI employees with an account can use the system as standard. Non-PSI employees must apply for an account for external users via their responsible contact person.
The system is only available as a tunnelling/proxy system. This means that after successfully logging into the system, there is NO active, usable shell available that can be used for a further connection to the PSI Lan.
A ‘setup-connection’ to hopx.psi.ch must be established at the start of use. This connection sets up access for the user on hopx.psi.ch. It must be interactive and kept open. Without this ‘setup-connection’, no connections to PSI-Lan are possible via hopx.psi.ch!
- Only one active ‘setup-connection’ to
hopx.psi.chis possible per user. (further information can be found below) - the ‘setup-connection’ can be combined with one or more port forwarding (see below)
- SSH clients (Putty, OpenSSH etc.) can be configured so that SSH connections to the PSI LAN are made via the ‘setup-connection’. (Keyword: SSH multiplexing, ProxyJump, Connection Sharing)
Note on OpenSSH:
The command
ssh -J <user>@hopx.psi.ch <user>@example-ssh-srv.psi.ch
does not work without a prior ‘setup-connection’, even if this is usually possible with OpenSSH!!!!
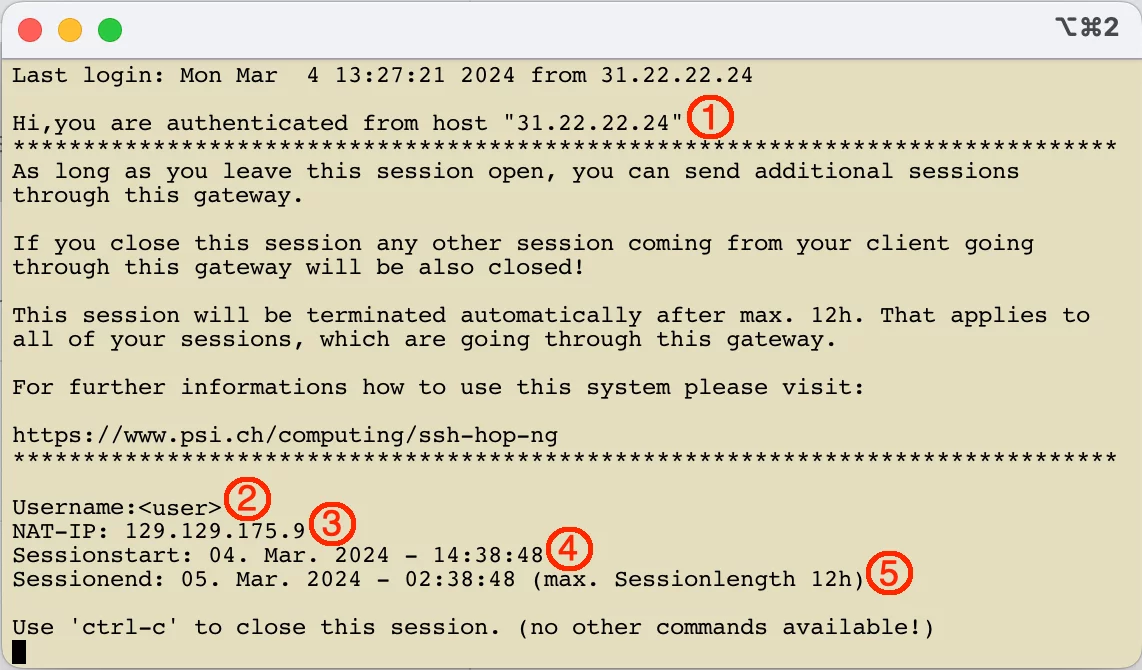
The following illustration shows the output after successful login.
The output after the login contains the following important information:
- The IP address of the client which established the connection to
hopx.psi.ch. - The user name which is used for the connection.
- The NAT IP address, which will be used for the connections established by the user through
hopx.psi.chto systems within the PSI network. - The date and time when the connection to
hopx.psi.chwas started - The maximum date and time until which the connection to
hopx.psi.chcan be held open. At this time (if the maximum session duration of 12 hours has expired) the connection tohopx.psi.chis automatically terminated. All connections to the PSI network going throughhopx.psi.chwill also be disconnected.
The connection to hopx.psi.ch can be terminated with ‘ctrl-c’. No further commands are available!
********* Attention ****************
If the ‘setup-connection’ to hopx.psi.ch is terminated while the connection(s) to an internal system are still active/open, these will also be terminated!!!
*********************************
Behaviour when establishing more than one ‘setup-connection’
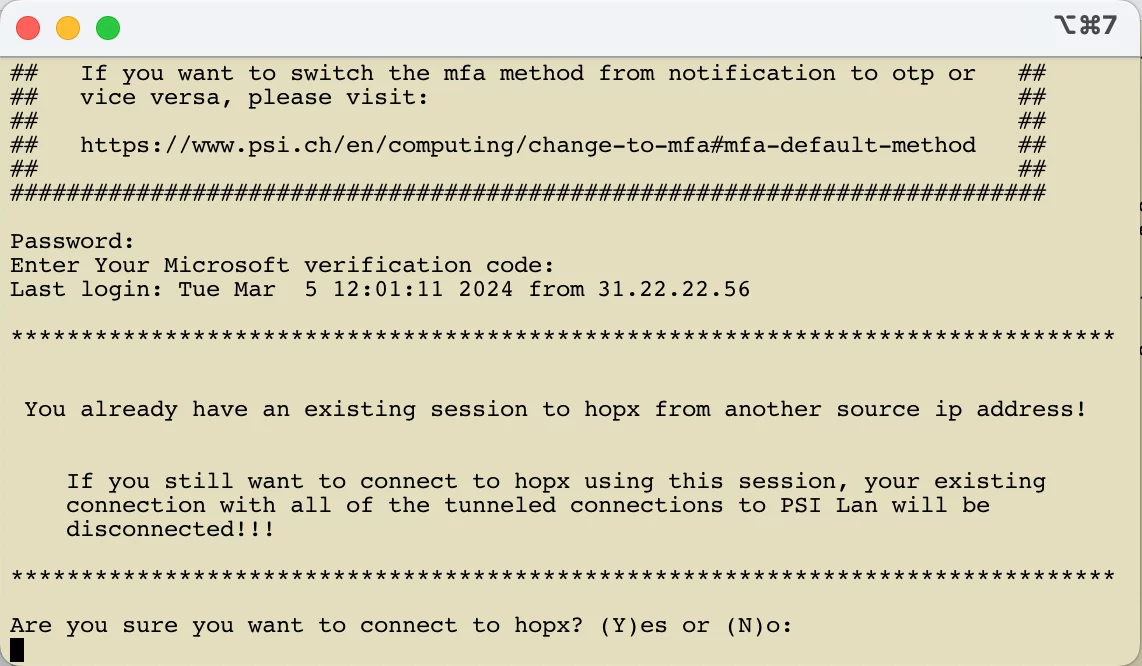
If a second ‘setup-connection’ is established to hopx.psi.ch using the same user name and the same source IP address, this connection will be terminated after successful authentication with a reference to the existing connection.
If a second ‘setup-connection’ is established to hopx.psi.ch using the same user name but a different source IP address to the existing connection, the user is given a choice after successful authentication. He can actually establish the second connection, but then the first connection and all associated tunnelled connections to the PSI network will be disconnected. Or he can terminate the second connection and continue working with the first. The answer to the question must be ‘Y’, ‘y’, ‘N’ or ‘n’.
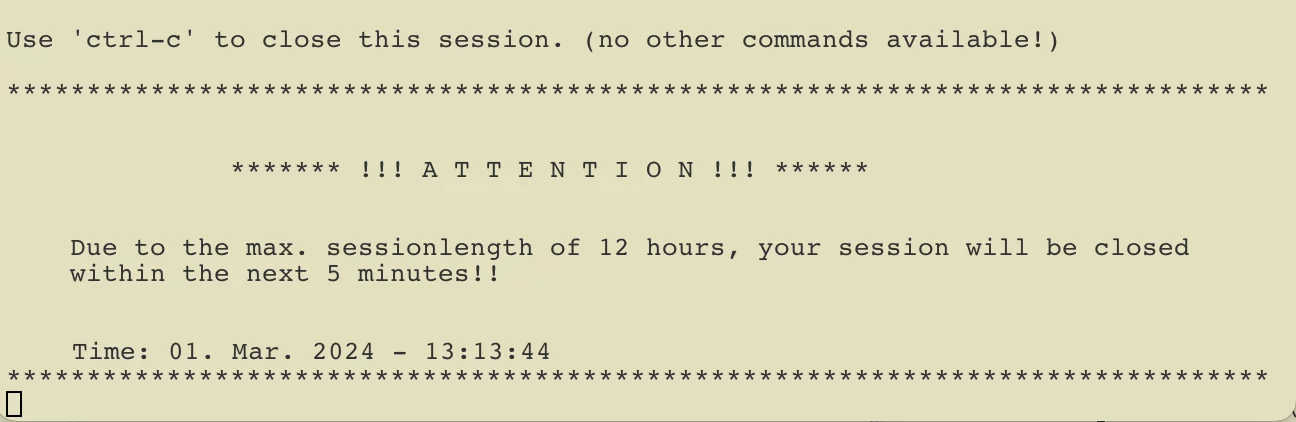
Maximum session duration of 12 hours
The duration of the active connection to hopx.psi.ch is limited to a maximum of 12 hours, similar to VPN access. The maximum time until which the connection can remain active is displayed after an successful authentication (see above). In the same window, five minutes before the connection is terminated, a message is displayed indicating that the connection is about to be terminated.
********* Attention ****************
If the connection to hopx.psi.ch is terminated while the connection(s) to an internal system are still active/open, then all other connections will also be terminated when the connection to hopx.psi.ch is terminated!!!!
***********************************
Note on the possible tunnel connections
Please note that not all users of the system have the same access rights. Depending on the type of the user account, different connections are possible via the system.
PSI employees
PSI employees can tunnel the following TCP connection to the PSI LAN via hopx.psi.ch:
| TCP port number | is used by |
|---|---|
| 22 | SSH |
| 80/443 | HTTP(S) |
| 445 | Windows File Server (z. B. fs00, fs01 or fs02) |
| >1023 | e.g. für RDP, VNC etc. |
External users
External users can tunnel the following TCP connection to the PSI LAN via hopx.psi.ch:
- SSH connections to the
Merlin,RA,Login,MEGetc. clusters. - SSH connections to the experiment jump systems etc.
These SSH connections are only possible if you have the appropriate access rights. If you do not have these rights, please get in touch with your responsible PSI contact person.
If you require further connection options, these must be requested for you by your PSI contact person.
The previously generally valid access options for external users such as
| TCP port number | is used by |
|---|---|
| 22 | SSH |
| 3389 | RDP |
| 5900 | VNC |
will be gradually deactivated during the next weeks.
Note on the use of VS Code
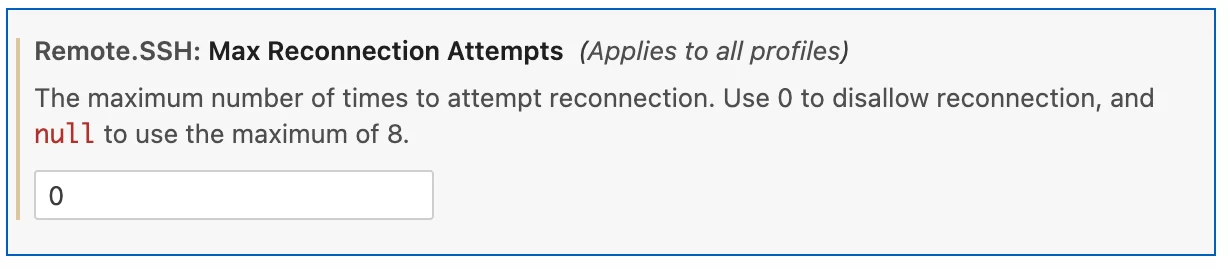
The remote SSH plugin of VS Code tries to re-establish an interrupted SSH connection several times due to the default settings. If a user was connected to several systems remotely via SSH and the connections were interrupted, VS Code tries to re-establish each connection automatically. This behavior can lead to many failed login attempts on hopx.psi.ch and in extreme cases to an automated blocking of the user account or the client IP address.
To prevent this, the number of automated connection attempts in the VS code must be significantly reduced.
To do this, "Max Reconnection Attempts" must be set to 0: